Host cobalt With YouTube Support
Posted on 10/31/2025 - hyperdefinedThis post shows how to self host cobalt with YouTube (and others) working. There are 2 parts to this guide: one for hosting on a server and one for running locally on your computer.
Both of these can help host your own cobalt instance to download media not currently working (like YouTube).
Thank you to this guide by ndzn for showing how to add the Clouldflare WARP stuff.
1. Hosting on a Server
Hosting on a server requires some changes made to using cobalt to work. Since you are on a server, all requests are made with a datacenter IP, which are not as “reputable.”
1.1 Setup Network
We need to first make a Docker network that allows for IPv6 support. Run this command below to make a new cobalt network.
docker network create --driver bridge --ipv6 --subnet fd00:c0ba:105::/64 cobaltThis creates a network for us to use for our cobalt instance that allows IPv6.
If you want to use redis/valkey or a HTTP proxy with your cobalt instance, please read below! If you don't, then you can skip to Section 1.2.
This assumes redis/valkey or your HTTP proxy is on your host machine and not in another container. If your redis/valkey or proxy is in another container, simply add those containers to the cobalt network and use the container’s name as the IP address. If not, follow below.
Create the cobalt network with a static IPv4 address, just so it doesn’t change. If you made the network earlier, you need to delete and remake it below. If the IP space clashes, change it to anything else.
docker network create --driver bridge --ipv6 --subnet fd00:c0ba:105::/64 --subnet 192.168.105.0/24 --gateway 192.168.105.1 cobaltOnce you create the network, you need to let traffic through your firewall. If you are using something like ufw, you can do so below:
ufw allow from 192.168.105.0/24 to any port 6379 comment "cobalt network to redis on host"You’ll need to do this for any port. The command above is for redis, but you need to do anymore if needed.
Once that is done, you can tell cobalt to use redis like so:
API_REDIS_URL=redis://192.168.105.1:6379You would use the gateway IP from the network you created. You also want to make sure your service is binded to 0.0.0.0 and NOT ALLOWED through your firewall.
1.2 Setup wgcf
Head over to https://github.com/ViRb3/wgcf/releases/latest and download one from the asset list based on your server.
You probably want the one labeled linux_amd64. Save this to your server like so:
# Replace version with the latest
wget https://github.com/ViRb3/wgcf/releases/download/v2.2.29/wgcf_2.2.29_linux_amd64If you are using a different architecture, find the one on the list and right click -> copy link and use that instead.
After you have it on your server, run the two commands below:
chmod +x ./wgcf_2.2.29_linux_amd64
./wgcf_2.2.29_linux_amd64 register
./wgcf_2.2.29_linux_amd64 generateThis will generate two files in the same directory: wgcf-account.toml and wgcf-profile.conf. Keep these files.
1.3 Setup Containers
We need to make changes to your current compose file that runs cobalt. We are going to add a new service to it, gluetun.
gluetun_cobalt_api:
image: qmcgaw/gluetun
container_name: gluetun_cobalt_api
sysctls:
- net.ipv6.conf.all.disable_ipv6=0
networks:
- cobalt
environment:
- VPN_SERVICE_PROVIDER=custom
- VPN_TYPE=wireguard
- WIREGUARD_ENDPOINT_IP=162.159.192.1
- WIREGUARD_ENDPOINT_PORT=2408
- WIREGUARD_PUBLIC_KEY=add_public_key
- WIREGUARD_PRIVATE_KEY=add_private_key
- WIREGUARD_ALLOWED_IPS=0.0.0.0/0,::/0
- WIREGUARD_ADDRESSES=172.16.0.2/32,2606:4700:110:80f7:d0bc:5a6f:226a:5169/128
cap_add:
- NET_ADMIN
devices:
- /dev/net/tun:/dev/net/tun
ports:
- 9000:9000
# Add this to the bottom of your compose file
networks:
cobalt:
external: true
WIREGUARD_ENDPOINT_IPis whatever the A record ofengage.cloudflareclient.comresolves to. You can double check if it changed here.
If you change your cobalt ports (under the ports section), change the port allocation on gluetun to match the ports you used for cobalt.
In the 3 environment variables, WIREGUARD_PUBLIC_KEY, WIREGUARD_PRIVATE_KEY, and WIREGUARD_ADDRESSES, you need to change these to the ones you generated from step 2. You can find them in the wgcf-profile.conf file. Find the two fields in the file PrivateKey and PublicKey. Set the two environment variables to them.
For WIREGUARD_ADDRESSES, copy and paste the addresses listed under Address in the wgcf-profile.conf file. Remove the spaces between them, so it’s a comma separated list.
# Notice there is no space
WIREGUARD_ADDRESSES=172.16.0.2/32,2606:4700:110:80f7:d0bc:5a6f:226a:5169/128Next, change your image from ghcr.io/imputnet/cobalt to git.canine.tools/canine.tools/cobalt:api. This image is a fork of cobalt to make changes to allow YouTube (and other services) to work. This is a fork maintained by myself and is used on cobalt.canine.tools.
Next, remove the ports section completely from cobalt. Add this to it as well:
network_mode: service:gluetun_cobalt_apiThis tells Docker to use our gluetun container as the network. Since it uses the gluetun container for networking, we have to move the port allocation to gluetun.
Lastly, we need to add these environment variables to cobalt:
CUSTOM_INNERTUBE_CLIENT=TV_SIMPLY
YOUTUBE_GENERATE_PO_TOKENS=1
YOUTUBE_USE_ONESIE=11.4 Final Compose
Here is an example of a final compose.yml. Adjust it as needed.
You may notice the YouTube session generator is missing. It's been outdated for a while now and not needed anymore.
You can remove it and remove the environment variables from cobalt.
services:
cobalt_api:
image: git.canine.tools/canine.tools/cobalt:api
restart: unless-stopped
container_name: cobalt_api
network_mode: service:gluetun_cobalt_api
environment:
# adjust as needed, use add your current variables here
- API_URL='https://api.url.example/'
# make sure the ones below stay
- CUSTOM_INNERTUBE_CLIENT=TV_SIMPLY
- YOUTUBE_GENERATE_PO_TOKENS=1
- YOUTUBE_USE_ONESIE=1
volumes:
# adjust as needed if you use cookies/keys
- ./cookies.json:/cookies.json
- ./keys.json:/keys.json:ro
healthcheck: # you can remove this
test: wget -nv --tries=1 --spider http://127.0.0.1:9000 || exit 1
interval: 30s
timeout: 5s
retries: 2
gluetun_cobalt_api:
image: qmcgaw/gluetun
container_name: gluetun_cobalt_api
sysctls:
- net.ipv6.conf.all.disable_ipv6=0
networks:
- cobalt
environment:
- VPN_SERVICE_PROVIDER=custom
- VPN_TYPE=wireguard
- WIREGUARD_ENDPOINT_IP=162.159.192.1
- WIREGUARD_ENDPOINT_PORT=2408
- WIREGUARD_PUBLIC_KEY=add_public_key
- WIREGUARD_PRIVATE_KEY=add_private_key
- WIREGUARD_ALLOWED_IPS=0.0.0.0/0,::/0
- WIREGUARD_ADDRESSES=172.16.0.2/32,2606:4700:110:80f7:d0bc:5a6f:226a:5169/128
cap_add:
- NET_ADMIN
devices:
- /dev/net/tun:/dev/net/tun
ports:
- 9000:9000 # adjust these as needed, this is the port to access cobalt
networks:
cobalt:
external: trueTo protect your instance, I recommend changing the port allocation to
127.0.0.1:9000:9000. This binds your instance to your network locally. If you want to access it remotely, setup a reverse proxy.Otherwise, your instance is public via the IP directly.
1.5 Host Your Own Web
This section shows how to host your own web of cobalt. The “web” part is the actual site, like cobalt.tools. Hosting your own web is very easy.
First, run the commands below. This clones cobalt’s source and install the dependencies for web.
git clone https://github.com/imputnet/cobalt.git
cd cobalt/web
pnpm iAfterwards, create a file in the web directory. You can use nano for this:
nano .envIn the file, include the contents below. Edit them as needed.
WEB_HOST=your-web-domain.com
WEB_PLAUSIBLE_HOST=your-plausible-host.com
WEB_DEFAULT_API=https://your-cobalt-api.com
ENABLE_DEPRECATED_YOUTUBE_HLS=trueThe first two are for using Plausible analytics. If you are not using it, you can remove those two. The only required environment variable needed is WEB_DEFAULT_API. This tells your web where to send requests to for media downloads. You can read more about the web environment variables on the cobalt web docs.
Next, run the build command.
pnpm run buildThis will build the site into web/build. This builds the site as a regular HTML site. All you have to do now is point your web server to this folder as the root directory.
2. Hosting Locally
This section covers running a local instance of cobalt on your own computer. This is recommended as your home internet is a residential IP, which is more “repeatable” and will be blocked less.
2.1 Install Things
You will need a few things installed. This guide is assuming you are on Windows.
- git
- Choose
Git for Windows/x64 Setup
- Choose
- Node.js
- At the bottom of the page, choose
Windows Installer (.msi)
- At the bottom of the page, choose
Download and install both of these.
After you have both installed, open up Terminal (don’t use Command Prompt). Copy and paste this command below into Terminal and enter:
npm install -g pnpm@latest-10This installs pnpm, which cobalt uses.
2.2 Setup cobalt
Run the commands below in Terminal in order (line by line). Keep Terminal open.
cd "$env:USERPROFILE\Desktop"
git clone https://git.canine.tools/canine.tools/cobalt.git
cd cobalt/api
notepad .envThis clones the cobalt source onto your desktop from my custom fork. This is a fork maintained by myself and is used on cobalt.canine.tools. It opens Notepad to create a .env file. Notepad will tell you the file does not exist, make sure to tell it to make it.
In Notepad, copy and paste this below:
API_URL=http://localhost:9000/
CUSTOM_INNERTUBE_CLIENT=TV_SIMPLY
YOUTUBE_GENERATE_PO_TOKENS=1
YOUTUBE_USE_ONESIE=1Save the file (Control + S) and close Notepad. Run these commands in the same Terminal Window.
pnpm install
pnpm startIf everything worked, you should see this similar output. Keep this window open.
cobalt API ^ω^
~~~~~~
version: 11.5
commit: 59cf8b4e5cf8db685cf20863fb85c0c70a9f96e8
branch: main
remote: canine.tools/cobalt
start time: Sat, 13 Dec 2025 00:51:13 GMT
~~~~~~
url: http://localhost:9000
port: 9000Once you see this, cobalt is now running locally on your computer.
2.3 Use It
Head to https://cobalt.tools in your browser. Head to Settings > instances and enable use a custom processing server. Paste in the text box: http://localhost:9000. Click the check mark next to it. You will see a warning, please take the time to read and understand it!
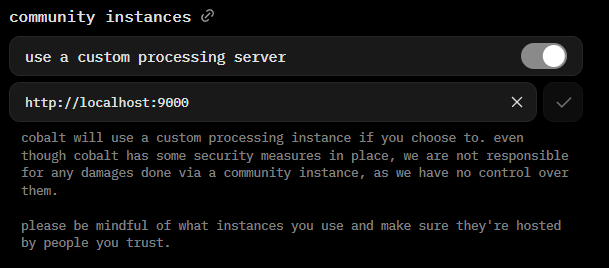
Afterwards, you are all set. Try to download media like normal!
This custom processing server will only work when cobalt is running. When the Terminal window is closed, make sure to disable the custom processing server (the same place you enabled it) on https://cobalt.tools.
When you want to run cobalt on your computer again, run the commands below.
cd "$env:USERPROFILE\Desktop\cobalt"
cd cobalt/api
pnpm install
pnpm runMake sure to re-enable “use a custom processing server” under Settings > instances on https://cobalt.tools.
I need help!
Join the cobalt Discord and ping @hyperdefined for help. You can also post for help under #cobalt-self-hosting. There is a wonderful group of members in the Discord to help out!